Cisco recently cautioned about a security weaknesses on some versions of IOS and IOS XE-based routers, switches and appliances. The risk is related to a certain type of password (Type 4) that could allow an authenticated remote attacker to access sensitive information on a targeted device.
Cisco recommends to check whether such passwords exist on your Cisco devices and to replace them with Type 5 passwords.
While Cisco has provided a method to test devices for existence of these problematic passwords, you may still want a way to ensure that such passwords are not introduced anytime in the future.
- Decrypt Cisco Secret 4 - wavethereal Originally developed to decrypt the 'encGroupPwd' variable in PCF files. This tool has evolved and can also decode Cisco type 7 passwords and bruteforce Cisco type 5 passwords (using dictionary attacks). Enable and Enable Secret password on CISCO Switch.
- No enable secret I'm playing with the password commands to make it clear. I've enable secret password now what I want to know is how to turn it off. Sorry noob here sir.
Cisco Type 7 Password Decryption. One fundamental difference between the enable password and the enable secret password is the encryption used. The enable password is stored by default as clear text in the router or switch’s running configuration. Enable and Enable Secret password on CISCO Switch. March 8, 2016 by virdih Leave a Comment. ENABLE SECRET PASSWORD. Enable password uses a weak encryption algorithm. To overcome this situation, we use enable secret password on the device. When both enable password and enable secret password are configured, enable secret password is used to. HiAny have a Cisco Router password decryption tool or url. enable secret level 5 not 7! I really need it. Unfortunately, it is impossible to reverse level 5 passwords.
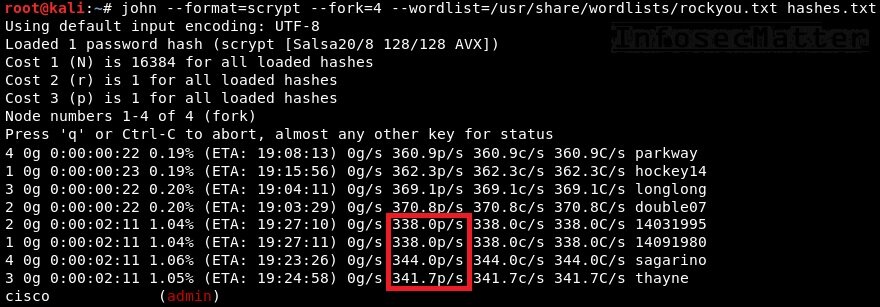

Decrypt Cisco Type 4 Password Online
Here's a custom device configuration test that we developed to identify any Type 4 passwords across your router inventory and also to alert if such a password is mistakenly configured in the future.
Assuming your routers are defined in SecureTrack, follow these instructions to test them:
- Add the custom test by running this command on the SecureTrack server:
curl -k -u <user>:<password> -X POST -d '<dcr_test_concrete><groupId>8</groupId><id/><name>Forbid Type 4 Passwords</name><isActive>true</isActive><isDefault>true</isDefault><risk>3</risk><severity>3</severity><testDef><description>Verify that Type 4 passwords are not configured.</description><expression>^(enable secret 4|username.*secret.4)[^n]*</expression><id/><input>running_config</input><isCustom>true</isCustom><mustContain>false</mustContain><name>Forbid Type 4 Passwords</name><products><device>IOS</device><id>1</id><vendor>Cisco</vendor></products><remediation>Replace Type 4 passwords with Type 5 passwords.</remediation><testDefUid>CU001</testDefUid><type>line_match</type></testDef><testUid>CU001</testUid></dcr_test_concrete>' -H 'Content-Type:application/xml' 'http://localhost:8080/securetrack/api/dcrTests/custom' - Create a new device configuration report under Reports
- Enable the new custom test:
- Save and run the report
- A properly configured device should pass the test like this:
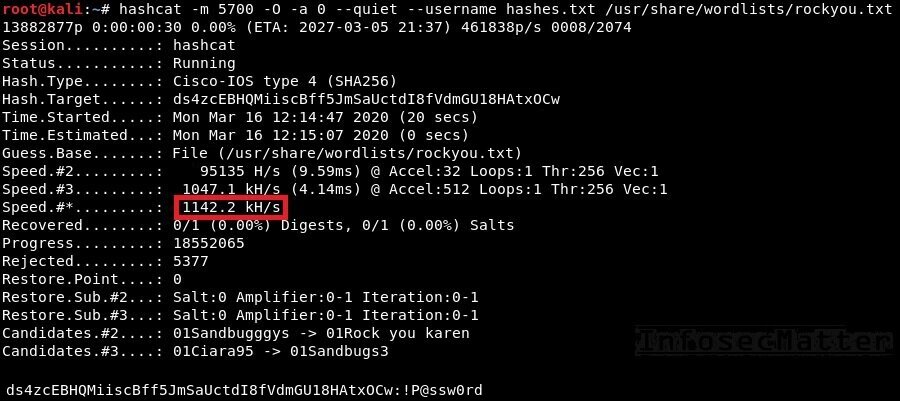

Decrypt Cisco Secret 4 Walkthrough
Enable Password (not enable secret), User passwords and most other passwords like VTY Password, Console Password, AUX Password in Cisco IOS configuration files are encrypted using a scheme that is very weak by modern cryptographic standards. Type 7 Passwords are not secure and can easily be decrypted. Cisco type 7 Password could be identifying as a password in the configuration file with a '7' in the second to last field. A Cisco Type 7 Passwords is encrypted using Cisco's weak proprietary algorithm.
(not enable secret), User passwords and most other passwords like VTY Password, Console Password, AUX Password in Cisco IOS configuration files are encrypted using a scheme that is very weak by modern cryptographic standards. Type 7 Passwords are not secure and can easily be decrypted. Cisco type 7 Password could be identifying as a password in the configuration file with a '7' in the second to last field. A Cisco Type 7 Passwords is encrypted using Cisco's weak proprietary algorithm.